For contractors in the defense industrial base (DIB), from start-ups to Fortune 500 companies, the cloud has presented an opportunity to design an environment that allows them to process, store, and transmit Controlled Unclassified Information (CUI) in a compliant manner. However, while many may look to the cloud as a cure-all for complying with security requirements, contractors must be aware of their responsibility for control implementation and management along with selecting an environment that is appropriate for the information associated with their Department of Defense (DoD) contract.
When considering utilizing the cloud, contractors should start by consulting the wording of DFARS 252.204-7012 which states, in relevant part:
“If the Contractor intends to use an external cloud service provider to store, process, or transmit any covered defense information in performance of this contract, the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline and that the cloud service provider complies with requirements in paragraphs (c) through (g) of this clause for cyber incident reporting, malicious software, media preservation and protection, access to additional information and equipment necessary for forensic analysis, and cyber incident damage assessment.”
While the clause does not specifically require that a FedRAMP authorized environment be utilized, only that the cloud service provider (CSP) meets equivalent requirements, it is in the contractor’s best interest to contract with a CSP that provides FedRAMP authorized environments and services to limit risk and complexity. Each of the two main CSPs, Microsoft Azure and Amazon Web Services (AWS), both offer various FedRAMP authorized environments that are appropriate to handle unspecified CUI through export-controlled information. Additionally, each CSP has developed a suite of programs that operate within their environments that provide services to assist contractors with managing user access, logging and monitoring events, identifying vulnerabilities, enforcing configurations, and meeting other NIST SP 800-171 requirements.
As part of the CSP selection process, contractors should refer to the platform’s customer responsibility matrix (Azure, AWS) to understand what actions are performed by the CSP that either fully or partially meet security requirements and which requirements are the full responsibility of the customer. It may come as a surprise that by AWS’s and Microsoft’s own accounting, only 18 – 24% of the controls are fully met by the CSP, as seen in the charts below which summarize the customer responsibility matrices.
Summary of Customer Responsibility Matrices by AWS and Azure
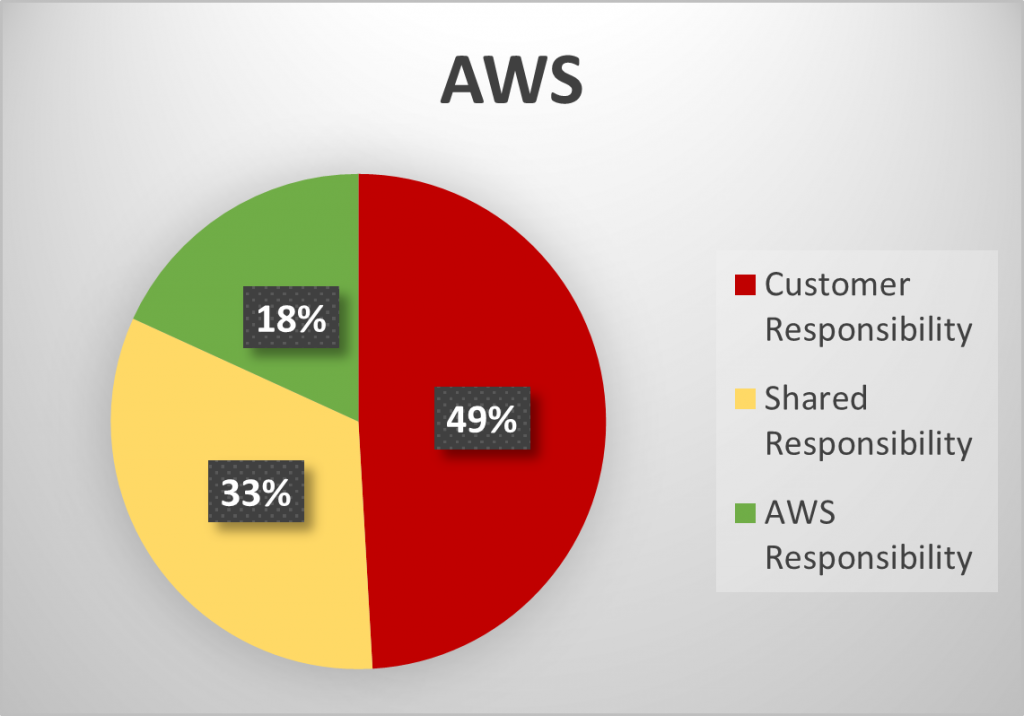
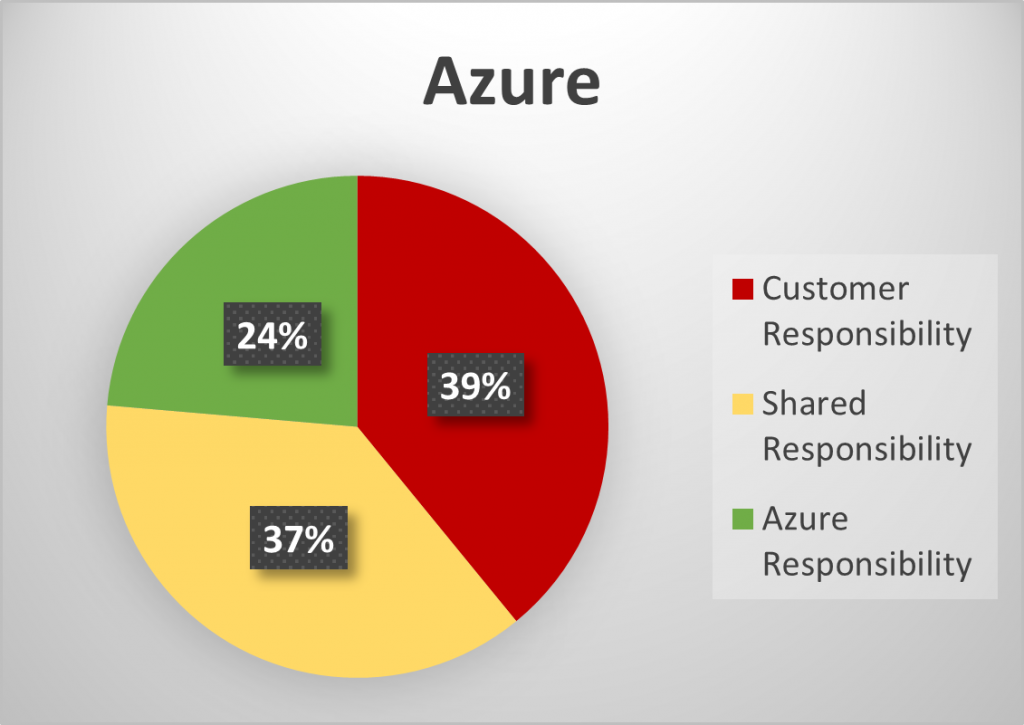
Taking a closer look, as you can see in the below graphs, the domains that the CSPs primarily satisfy are Physical Security, Maintenance, and Media Protection. Where domains contain a majority of shared responsibility controls, the CSP provides tools and services that may assist the contractor in meeting control objectives, but it is the responsibility of the contractor to ensure that the services are enabled, appropriately configured, and managed on an ongoing basis. This can be seen largely in the Audit and Accountability, Configuration Management, and System and Communications Protection families.
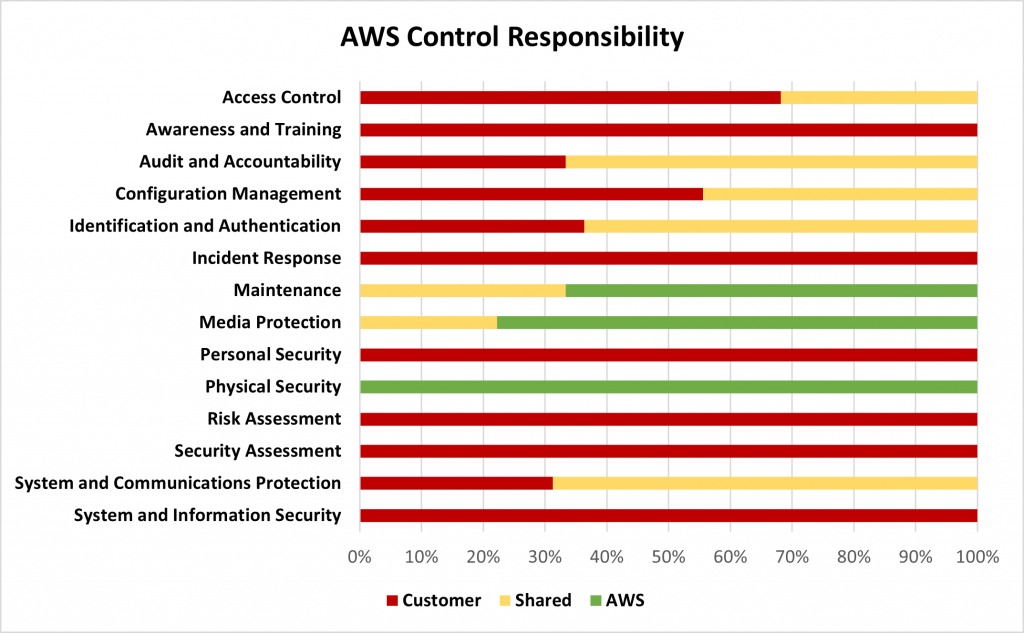
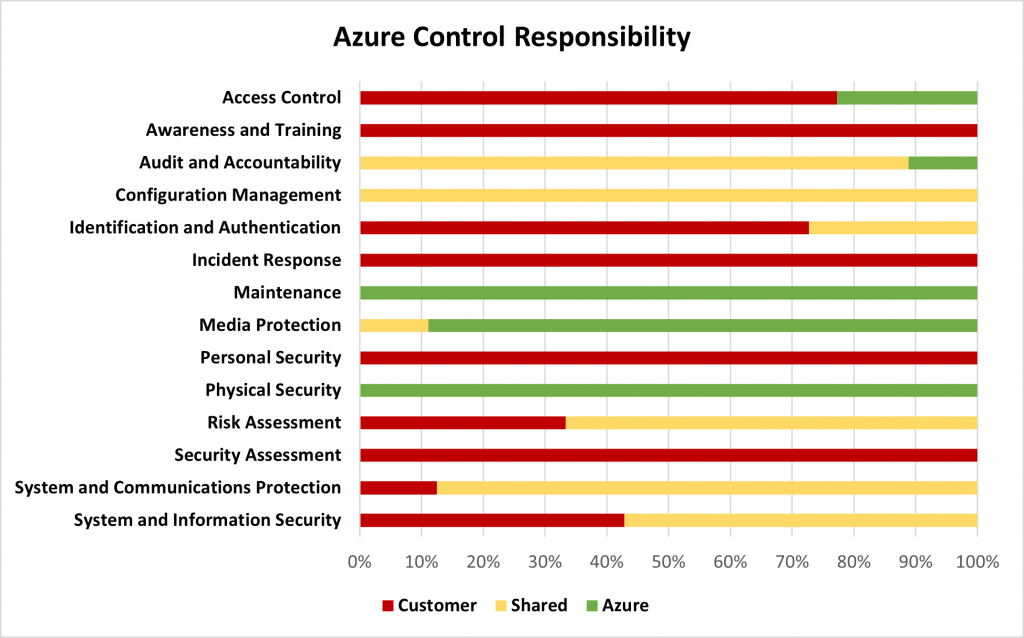
Readers should note that there are some differences in how Microsoft and AWS categorize certain controls. For example, in the Access Control family, Azure considers the controls around wireless access and connection of mobile devices to be met by the environment while AWS considers these to be shared responsibilities. Additionally, for the Configuration Management family, Azure considers all controls to be shared responsibilities while AWS considers just under half of the controls to be shared between the customer and the CSP. As a sound practice, contractors should take care to understand how their planned use of the environment will relate to organizational and CSP control processes and where actions of users and administrators span environment boundaries.
Another consideration that is important for smaller or less mature organizations is that while the CSP will aid in meeting many of the technical control requirements, the contractor is still responsible for policies, procedures, and the all-important System Security Plan, which is the key compliance artifact. A primary objective of the DoD in issuing the Safeguarding CDI rule (252.204-7012) and developing the Cybersecurity Maturity Model Certification (CMMC) framework (252.204-7021) was to enhance the cyber maturity of companies in the defense industrial base, and in many cases, that starts with a strong foundation of processes supported by qualified personnel and adequate resources. Contractors cannot rely on CSPs to provide this foundation, and failure to take ownership in this regard will result in challenges when faced with a third-party assessment. This leads into the question that has arisen with the issuance of 252.204-7021 and the impending CMMC requirement, and that is the question of reciprocity with the FedRAMP authorization. Contractors have been hopeful that by utilizing a FedRAMP authorized cloud environment they would be able to meet the requirements to obtain the necessary certification. However, while the DoD is continuing to evaluate this concept, initial signs are that one-for-one reciprocity is not likely, and this can be attributed to the points we have discussed above. Even when a compliant cloud is being utilized, the contractor is required to be actively involved in control implementation, and therefore, the DoD has expressed that an assessment will likely still be required.
In conclusion, on top of all the traditional benefits that the cloud has provided commercial businesses, such as scalability and flexibility, it offers federal contractors with an opportunity to design environments to securely manage CUI and meet their compliance requirements. For smaller companies without the resources to invest in equipment, licenses, and personnel, the cloud is essential to their operations and business strategy. Despite its potential and many useful tools, the cloud is not a panacea for federal contract compliance and contractors must recognize that they are ultimately responsible for the safeguarding of information under their contracts, regardless of where it is hosted.
Chess Consulting has experience assisting DIB contractors of all sizes to understand how the requirements of DFARS 252.204-7012 and 252.204-7021 impact their organization. Our extensive experience assisting contractors with government contract compliance matters paired with a deep understanding of cybersecurity and information security practices allows us to provide our clients with a holistic approach to compliance. Contact a Chess professional today.
